Setting up a permission structure
AccessOwl offers three different ways to map out an application permission structure:- 1. Standard Permissions
- 2. Objects and Roles
- 3. Multi-level Objects
One set of roles/permissions per application
This is the simplest form where the application has a set of roles/permissions (entitlements). You can specify whether only one entitlement can be selected or multiple roles can be selected.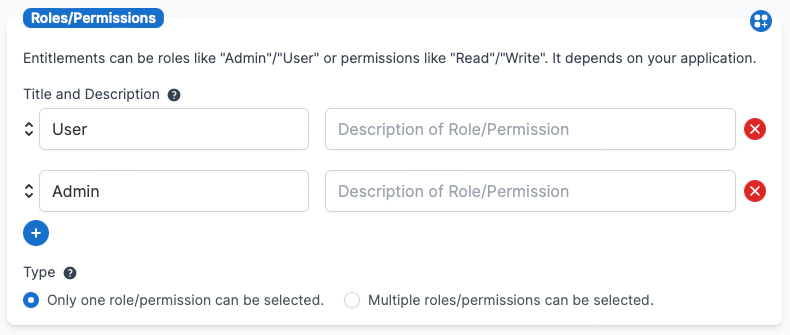

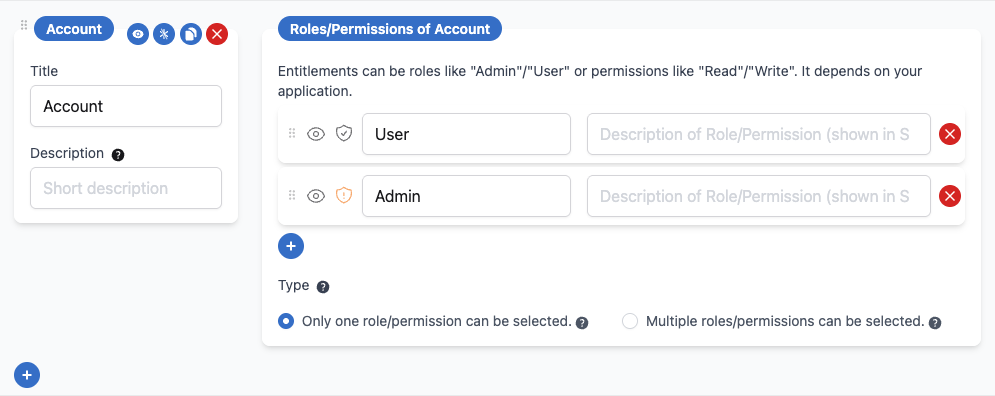
Mandatory Objects
Some applications require users to have a base-level access before they can request additional permissions. For example, a user might need a Salesforce “Profile” before they can request specific licenses, or a 1Password “Account” before they can access individual vaults. You can mark root-level objects as mandatory to enforce this dependency. When an object is marked mandatory:- Users must either already have access to the mandatory object, or include it in their request
- If a user tries to request other permissions without the mandatory object, they’ll see a validation error listing the required roles/permissions
- Approved requests will wait in a “Pending dependency” status until all mandatory objects are provisioned
How to Configure
In the Roles/Permissions editor, toggle the asterisk icon next to a root-level object to mark it as mandatory. The fieldset gets a red left border so that mandatory objects are easy to spot, and the filled/slashed asterisk shows whether the object is required or optional.Only root-level, requestable objects can be marked as mandatory. Nested objects cannot be set as mandatory.